Techsyspro is an intelligent edge security platform that surrounds and protects your entire architecture (core, cloud, and edge) to thwart attackers and mitigate threats wherever they arise.
Boost Your Business with Our Coordinated Managed Security Services
From advanced threat detection to proactive risk management, Techsyspro fortifies your website against the ever-evolving landscape of cyber threats. We don’t just protect your digital assets—whether it’s your website, Android or iOS applications, internal and external networks, APIs, or servers—we build a foundation of trust and confidence.
Our advanced security protects against online threats, giving you peace of mind to grow your business. Trust Techsyspro for reliable, professional protection and secure your site today.
In the dynamic realm of online security, choose Techsyspro for an unwavering shield that empowers your digital ventures and fosters a secure environment for growth.

Web Applcation Pentesting
Mobile Applcation Pentesting
API Pentesting
NetworkPentesting
Source code Review

What is VAPT ?
Combination of machine and human-led techniques
Vulnerability Assessment and Penetration Testing, or VAPT for short, is a thorough security testing methodology designed to find and fix cyber security flaws. By integrating penetration testing and vulnerability assessment, VAPT offers a comprehensive analysis to improve the cyber security of your company.
Depending on the geographic area, VAPT may refer to a single, unified offering or a bracket for several different services. Anything from automated vulnerability assessments to human-led penetration testing and red team activities might be included in VAPT as a whole.
Some of The Benifits of VAPT
Identifying vulnerabilities | Identifying vulnerabilities | Regulatory compliance | Improving security | Enhancing incident response | Continuous monitoring
Web Application Pentesting
Identifies Vulnerabilities in your Web Application
A cybersecurity technique called web application penetration testing is actively analyzing and evaluating an online application’s security. Finding and fixing vulnerabilities that might be used by hostile actors to jeopardize the availability, confidentiality, or integrity of the program and its data is the main goal of web application pentesting.
Why you should go with Web Application Pentesting
Vulnerability Identification | Risk Mitigation | Compliance Assurance | Sensitive Data Protection | User Trust and Reputation Management | Financial Loss Prevention | Business Continuity | Strategic Decision-Making | Security Cost Reduction | Continuous Improvement


Mobile Application Pentesting
To identify Vulnerabilities in Mobile Application
Mobile Application Pentesting is a comprehensive security evaluation that mimics actual assaults to find weaknesses in mobile applications. By identifying intricate security vulnerabilities in the application’s code, communication protocols, and server-side components, this procedure goes beyond simple testing. Our objective is to stop illegal access, data breaches, and other security events that can jeopardize the privacy of your users and the standing of your company.
Some of The Importance of Mobile App pentesting
Safeguarding user information | Detecting and resolving vulnerabilities | Preventing unauthorized access | Addressing platform-specific risks | Reducing financial risks | Defending against threats specific to mobile devices | Maintaining compliance | Adjusting to changing threats | Fostering user trust | Enhancing incident response readiness
API Pentesting
Discover Security Weaknesses and Protect your APIs
API Penetration Testing, also known as the practice of assessing an Application Programming Interface’s (API) security in order to find flaws and vulnerabilities that hackers could exploit is called API Penetration Testing, often referred to as API Security Testing. Finding weaknesses in API endpoints, parameters, and data validation is the aim of API penetration testing. Detecting unauthorized access and data breaches, adhering to industry laws (OWASP, PCI-DSS, and HIPAA), evaluating the robustness of APIs to distributed denial-of-service (DDoS) and denial-of-service (DoS) assaults, and implementing security measures and authentication procedures are all included.
Why API Pentesting is important ?
Data protection | Securing data transmission | Preventing unauthorized access | Evaluating authorization mechanisms | Reducing business risks | Ensuring compliance | Scalability and performance | Safeguarding against API-specific threats | Fostering trust with clients and partners | Continuous security improvement | Identifying and resolving vulnerabilities | Enhancing incident response readiness


Network Pentesting
To protect Organizations from inside Vulnerabilities
Network penetration testing, often known as network pentesting, is a cybersecurity technique where experts mimic assaults carried out by actual hackers or malevolent actors. This aids in identifying security holes and weaknesses in the network’s defenses. In addition to numerous endpoints and devices, such as servers, PCs, mobile devices, and Internet of Things (IoT) devices, networks are extremely complex and comprise a mix of WAN, LAN, and Wi-Fi. They also include intrusion prevention systems (IPS) and firewalls, among other security technologies. Any one of these elements could have a flaw that hackers might take advantage of to enter the network without authorization. Network penetration testing’s primary goal is to assess the security of the present network and find security flaws before a real cyberattack occurs.
Importance of Network Pentesting
Vulnerability Identification | User and Customer Trust | Risk Mitigation | Data Breach Prevention | Compliance Needs | Keeping Up with Changing Threats | Incident Response Readiness | Constant Improvement | Enhancement of Security Posture | Third-Party Risk Management | Defense Against Exploits
Source Code Review
Discover Secure standard of Code
Source Code Review is an in-depth examination of your application’s codebase to find any security flaws, errors, and inefficiencies. At Techsyspro, we methodically examine the code’s dynamic and static components to find any vulnerabilities that an attacker may exploit. To make sure that every security issue is found and successfully fixed, our team use both automatic tools and human methods. Reviewing the source code is also crucial for finding and fixing security flaws that conventional testing could miss.
Why Source Code Review is important ?
Data protection | Securing data transmission | Preventing unauthorized access | Evaluating authorization mechanisms | Reducing business risks | Ensuring compliance | Scalability and performance | Safeguarding against API-specific threats | Fostering trust with clients and partners | Continuous security improvement | Identifying and resolving vulnerabilities | Enhancing incident response readiness


Cloud Pentesting
To protect your cloud assets today!
Cloud Penetration Testing is an essential procedure for assessing the security of cloud-based infrastructure and apps. Sophisticated security experts try to find flaws, setup errors, and vulnerabilities in cloud networks by mimicking actual assaults. Finding possible security threats and offering practical suggestions to improve the overall security posture of cloud-based systems are the main goals.
Importance of Cloud Pentesting
Data protection | Compliance | Customer trust | Reduced costs | Centralized security | Ease of scaling
Cyber Security Audit
Assess the strength of your digital defenses
A cybersecurity audit is a thorough assessment of your company’s IT procedures, policies, and infrastructure to make sure they adhere to security guidelines and are impervious to online attacks. In order to help you comply with industry rules and strengthen your defenses against cyberattacks, our audits examine both technological and procedural controls to find weaknesses.
Key Benefits of Performing Cybersecurity Audit
Protecting reputation | Identifying vulnerabilities | Assessing risk | Improving security posture | Saving costs | Providing assurance | Developing strategies | Network Security Audit | Application Security Audit | Incident Response Readiness Assessment | Endpoint Security Audit | Cloud Security Assessment | Compliance and Policy Review | Examining user security


Secure Product Delivery
Safeguarding organization's reputation & competitiveness
Delivering software products while prioritizing and guaranteeing the security of the complete development lifecycle is known as “secure product delivery.” In order to detect, lessen, and avoid security risks and vulnerabilities, it entails including security procedures and safeguards at each phase of the software development process. Creating software that is resistant to cyberattacks, safeguards user information, and upholds the application’s integrity and confidentiality is the aim of secure product delivery.
Why Secure Product Delivery is Important?
Ensuring business continuity | Safeguarding user data | Reducing cybersecurity risks | Keeping up with changing threats | Preserving user trust | Boosting competitiveness | Adhering to regulations | Safeguarding intellectual property | Preventing financial loss | Fostering trust in digital transformation | Maintaining reputation | Ensuring customer satisfaction
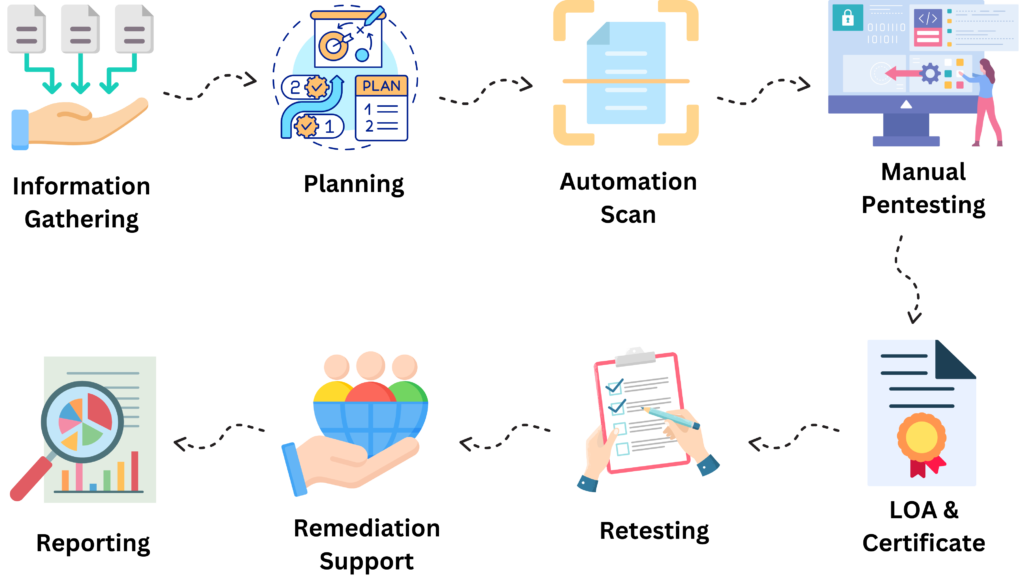
Our Penetration Testing Proceess
Technologies & Tools We using for VAPT Services
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Businesses We Serve with Our Services
On-Demand Solutions
Education & e-Learning
E-Commerce & Retail
Shipping, Logistics & Distribution
Healthcare & Fitness
Real Estate
Travel & Hospitality
Food & Restaurant
Social Networking
Gaming
Why Choose Us
Your Website's Trusted Protection Begins Here
- We are committed to providing proactive solutions and ensuring the greatest degree of protection is applied to your digital assets.
- Techsyspro is a digital security white hat hero.
- We are a cybersecurity firm that specializes in penetration testing for cloud networks, external networks, mobile apps, APIs, and Internet of Things (IoT) devices.
- Our team is made up of innovative problem solvers that put forth endless effort to identify security flaws.
- We have assisted businesses all over the world, from start-ups to multinational corporations, in strengthening their defenses against online attacks.
Our Approach to VAPT
To deliver cybersecurity services, Techsyspro combines state-of-the-art technology, industry-specific knowledge, and a customer-centric approach.
Tailored understanding
Open and Honest Reporting
Accurate Evaluations
Continuous Assistance
Testing for Strategic Penetration
Innovation in Security
